Setting up SSO(with Okta)
This guide walks you through setting up Single Sign-On (SSO) with Okta for seamless access to DriveHub. It outlines the required configurations in both Okta and DriveWealth for a secure, integrated login experience.
Create SSO App in Okta
- Create a new application by clicking ‘New App Integration’ button, then selecting ‘OIDC - OpenID Connect’ then select ‘Web Application’ for application type. Select Next to move forward.
- Fill in the details for the application.
- Enter a name for the application.
- Add sign in redirect URI.
- Skip group assignments if you want to do it later.
- Share the ClientID, Client Secret and tenant URL securely with DriveWealth.
- Update the group mapping on the Sign-On tab. (Recommend this be set to ‘Starts With’ and ‘DriveHub’)
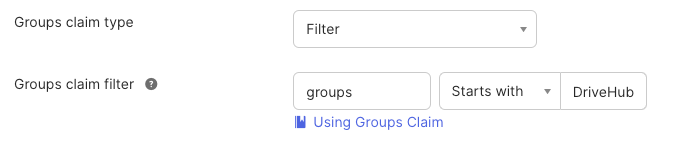
Using the wildcard “*” and having a user with over 100 groups can break the authentication which is why its recommended to narrow what groups are sent.
Refer: Okta Help Center
Create Bookmark App
- In Okta, go to the Browse App Integration Catalog and search for Bookmark.
- Click on Bookmark App and Add Integration.
- Enter a name such as DriveHub
<environment name> - Enter the URL for DriveHub.
- Click done and assign users.
Create SCIM App in Okta
-
In Okta create a new custom application.
-
Select Secure Web Authentication (SWA).
- Enter a name for the application.
- Enter the login page URL, this URL is not used and doesn’t matter but has to have a URL. You can enter https://www.auth0.com.
- Check the box to hide the application from users.
- Check the box under app type to mark that this is an internal application.
- Click finish
-
On the general tab, change provisioning from ‘None’ to ‘SCIM’ then save.
-
Click the Provisioning tab.
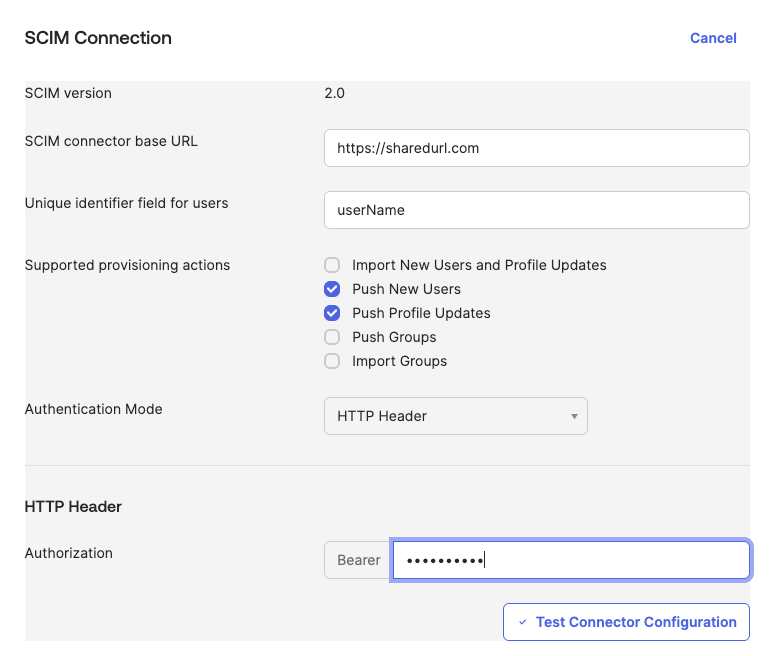
- Enter the SCIM connector base URL that was shared.
- Enter userName for the unique identifier field for users.
- For supported provisioning actions, select ‘Push New Users’ and ‘Push Profile Updates’.
- For Authentication Mode, change it to HTTP Header.
- For the Bearer token, enter the token that was shared.
- Click ‘Test Connector Configuration’ to verify the connection works.
- Then click Save.
- Click on the To App tab.
- Check enable for ‘Create Users’, Update User Attributes' and ‘Deactivate Users’.
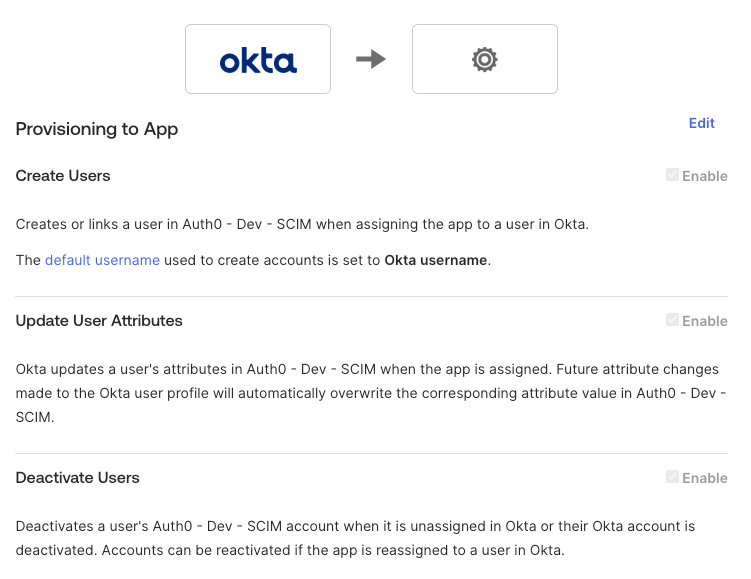
- From here you can add groups and assign users and they will sync with Auth0.
Creating The Role Sync
❗You will repeat this process for each role. Update display and variable names as appropriate.
- Navigate to Directory then Profile Editor and select “User (default)” or another user type if you chose.
- Click on “Custom” then click “+ Add Attribute”.
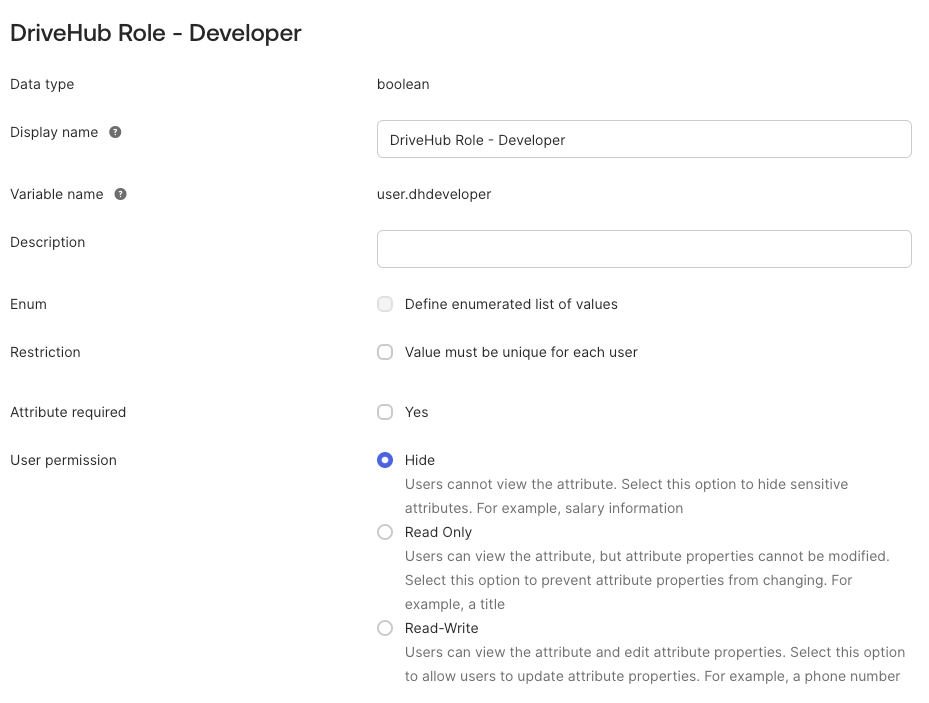
- Set the attribute to the following settings:
- Data type: boolean
- Display name: DriveHub Role -
<rolename>(Can be anything you want/need, just recommend) - Variable name: dh
<rolename>(Can be anything you want/need, just recommend) - Description: DriveHub Role (Can be anything you want/need, just recommend)
- User permission: Hide
- Click “Save Attribute”
- Click Profile Editor and search for the SCIM application.
- Click on “Custom” then click “+ Add Attribute”.
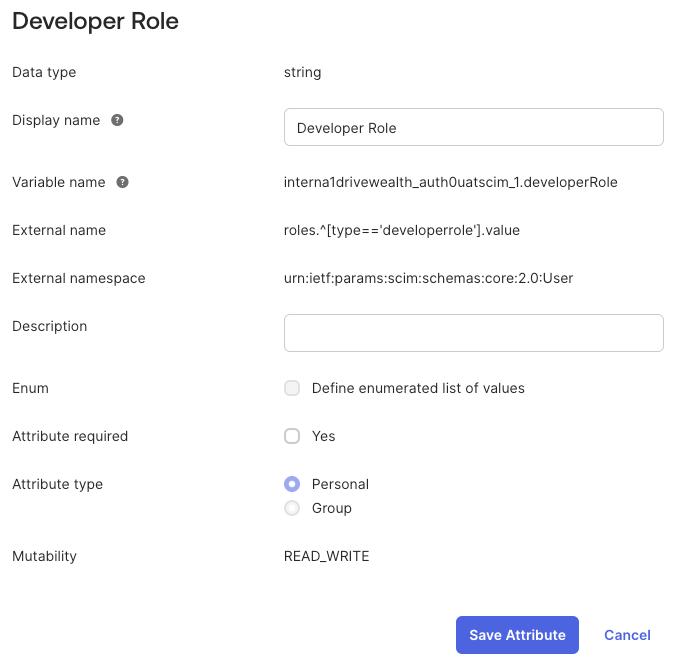
- Set the attribute to the following settings:
- Data type: string
- Display Name:
<rolename>Role - Variable name:
<rolename>Role - External name: roles. [type==
<rolename>role].value - External namespace: urn:ietf:params:scim:schemas:core:2.0:User
- Description: DriveHub Role
- Attribute type: Personal
- Click “Save Attribute”
- Click “Mappings” then click the user type you want to modify.
- Click Okta User to “name of your application”.

- Scroll to bottom and add the following to each role you want to map over.
(user.<booleanattributename>== true) ?<roleID>:''
Once your Okta SSO configuration is complete, users will be able to access DriveHub using their Okta credentials. If you have any questions or run into issues, please reach out to your DriveWealth Contact for support.
Okta Reference MaterialsAuth0 Okta Workforce Reference: Connect Your Auth0 Application with Okta Workforce Enterprise Connection
Auth0 SCIM Reference: Inbound SCIM for Okta Workforce Connections
Okta Role Sync Reference: Okta Help Center (Lightning)
Updated 6 months ago